(ABSTRACT) As electricity consumption rises and the shift toward sustainable energy continues, the power grid is undergoing significant changes. These advancements, while crucial, have also introduced new vulnerabilities, making the grid a prime target for cyberattacks. Such attacks can have far-reaching consequences, from financial loss to national security threats. Recognizing the critical role of energy infrastructure, both the U.S. Department of Homeland Security and the European Commission emphasize the need for robust cybersecurity measures and physical protection systems, like the TRANSFORMER PROTECTOR™, to safeguard key assets. By prioritizing failsafe solutions and implementing comprehensive disaster recovery programs, we can enhance the resilience and security of our power grid, ensuring stability across borders.
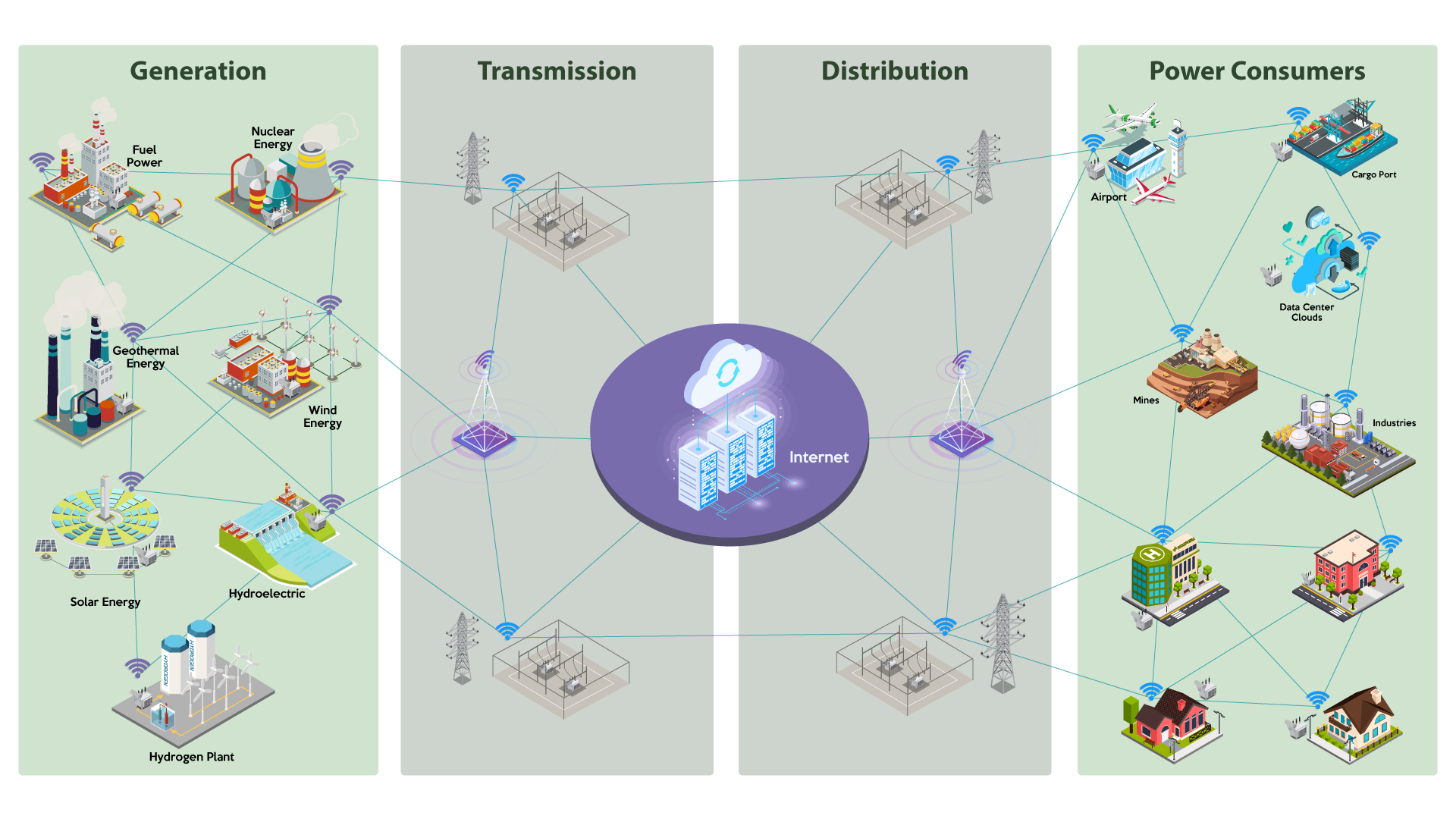
The power grid’s evolution over the past decades has been marked by the integration of new technologies and a shift towards more sustainable energy sources. This expansion has transformed the grid into a complex, interconnected system that spans across nations and continents, making it an essential component of critical infrastructure. Both the U.S. Department of Homeland Security (DHS) and the European Commission recognize the energy sector as uniquely critical, as its reliable operation underpins all other critical infrastructure sectors.
While technology has enabled enhanced monitoring, control, and maintenance of the grid, it has also expanded the attack surface for cyber threats. As the DHS has noted, “the Energy Sector provides one of the key lifeline-functions upon which all other critical infrastructure sectors rely—the Nation’s security and economy depend on it.” However, this interconnectedness also means that the grid is particularly vulnerable to cyberattacks, which, if realized, can have devastating consequences, including widespread power outages, economic disruptions, and even loss of life.
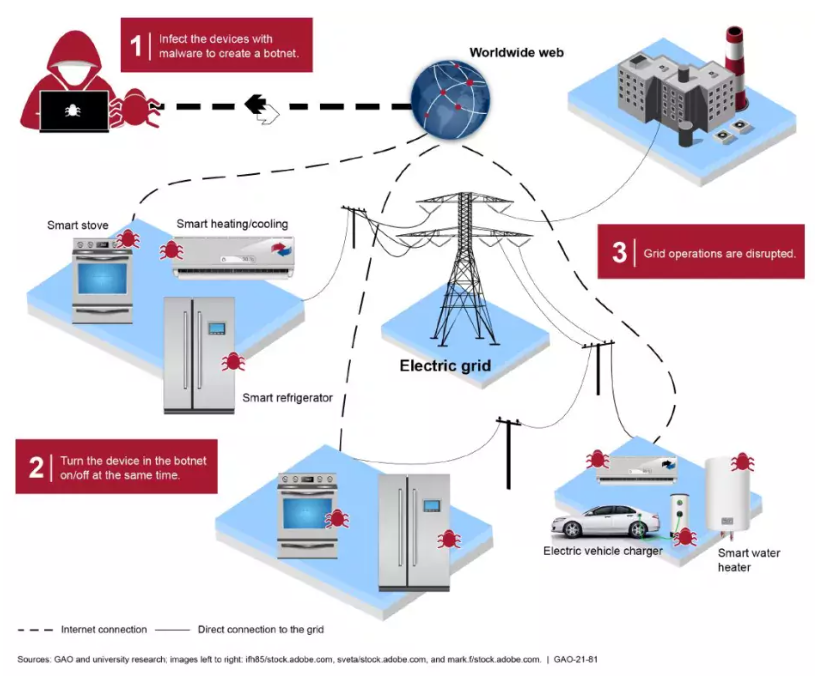
Understanding Cyberattacks: Motives and Consequences
Cyberattacks on the power grid typically fall into two categories: financial gain and political or strategic pressure.
Financially Motivated Attacks:
- Data Breaches: Cybercriminals infiltrate companies to steal valuable business information, company databases, and customers’ personal data.
- Ransomware: Attackers freeze operations or seize control of digital assets, demanding a ransom to restore access, causing significant financial harm.
Politically or Strategically Motivated Attacks:
- Grid Disruption: These attacks aim to interrupt or damage power grid assets, leading to widespread outages.
- Control Room Sabotage: Attackers may deploy tactics to disrupt control room operations, preventing timely responses to the attack.
- Asset Destruction: Key assets, such as transformers, can be targeted, leading to catastrophic failures and cascading effects across the grid.
The Actors Behind Cyberattacks
Coordinated groups of hackers, often linked to government security agencies, are responsible for many of these attacks. For instance, Sandworm, a group associated with the Russian government, has been implicated in several high-profile cyberattacks, including the disabling of Ukraine’s power grid in 2015. This incident left over 225,000 customers without power for hours and highlighted the real-world impact of cyber warfare.
The Threat Landscape According to DHS, the European Commission, and Industry Experts
The DHS, in its 2015 Energy Sector-Specific Plan, emphasizes the evolving nature of cyber threats, noting that “many critical infrastructure and essential functions—including hospitals, water and wastewater systems, transportation, and telecommunication—depend on the reliable supply and delivery of electricity and other fuels to operate.” This interdependency means that a cyberattack on the power grid can have cascading effects across multiple sectors, further amplifying the potential damage.
Similarly, the European Commission has developed a comprehensive strategy to bolster cybersecurity within the energy sector. According to the Commission’s 2020 Security Union Strategy, the initiative to “make critical energy infrastructure more resilient against physical, cyber and hybrid threats” aims to ensure that energy operators across Europe can operate securely in both physical and digital realms. This is particularly crucial given the unique challenges within the energy sector, such as real-time operational requirements and the integration of legacy systems with new technologies.
Moreover, the Commission’s first-ever network code on cybersecurity for the electricity sector, published in 2024, addresses the need for sector-specific rules to manage cybersecurity risks related to cross-border electricity flows. It underscores the importance of “a harmonized approach in the rapidly evolving knowledge field” to ensure that the cybersecurity measures implemented across the EU are effective and consistent.
Mitigation Strategies and the Role of TRANSFORMER PROTECTOR™
To safeguard the power grid, a combination of active and passive defense measures is essential. Active measures include real-time monitoring and rapid response to threats, while passive measures focus on preventing access and damage before an attack occurs.
A particularly critical and potentially catastrophic scenario arises when key assets, such as transformers, are compromised. If an attacker successfully manipulates protection schemes or blocks alarm signals, the result could be an uncontrollable overload, leading to transformer explosions. The European Commission’s emphasis on the importance of rapid reaction and the challenges posed by cascading effects within interconnected grids highlights the need for reliable physical protection systems.
To mitigate this risk, many utilities have adopted the TRANSFORMER PROTECTOR™. This passive mechanical system is immune to hacking, as it operates without electronic sensors or signals that could be manipulated. Instead, it activates in response to dynamic pressure following a short circuit, effectively preventing transformer explosions and fires. As recognized by NFPA code 850, the TRANSFORMER PROTECTOR™ safeguards critical components such as the tank, OLTC, bushing turrets, and oil cable boxes.
Conclusion
The recognition of the power grid’s vulnerabilities has underscored the need for comprehensive protection strategies. Implementing both active and passive defense tools is essential to preventing cyberattacks and their potentially devastating outcomes, which include financial losses, data breaches, operational disruptions, and even loss of life. Among these tools, the TRANSFORMER PROTECTOR™ stands out as a proven solution, trusted by over 2,500 clients in more than 80 countries worldwide. Its passive, mechanical nature makes it an invaluable addition to any cybersecurity and disaster recovery program, ensuring the reliability and safety of the power grid in the face of escalating cyber threats.
In alignment with the European Commission’s efforts, adopting such robust protection measures will help ensure a level playing field for energy operators across borders, enhancing both cybersecurity and the overall resilience of Europe’s energy infrastructure.




